10:37 AM Trojan !! What is it ? |
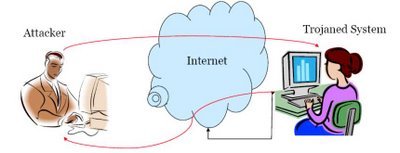
  The file may appear to be a photograph, a document, a sound file or even a game of some sort. When you try to open the file, it often appears as though nothing has happened. At this point, many users assume that the file "didn’t work” and forget the whole thing. In actual fact, you nay just have installed something quite nasty on your system, and chances are that the Trojan will make sure it runs every time you start your computer. Effectively you’ve just installed a backdoor into your system. Not only do you not know that it’s there, but it can be easily and discretely used without your knowledge or permission. Some of them may be relatively "harmless” to your system, and may simply use your computer as part of a co-ordinated Denial of Service attack on another system. Some of them may open up the possibility of someone accessing your machine, but may remain unused for years. Other Trojans pose a far greater effect to your computer and your data. Some may monitor your internet connection and grab your email addresses and access passwords. Perhaps your email will be intercepted, perhaps credit card details that you store or enter will be copied, or perhaps someone, somewhere, will simply have a wander through your hard drive, seeing if there’s anything of interest. If you install software, listen to music files, share data, receive email or surf the web, you’re at risk. An incredible fact is that even if your system really is well and truly isolated, is never updated, with no additional software ever being installed, with no connection to any outside line, the internet or a network of any kind, you still may be at risk. How? Someone, somewhere had to install the operating system and software onto your hard drive. As unlikely as it may be, it is still possible that a Trojan is lurking somewhere on your system. The fact that it has no means of doing anything isn’t the point… it may still be there. A virus is a small program that "adds itself” onto an existing program, and forms a modified file. Because of this it is difficult to detect, as no new or suspicious files will initially appear on the infected system. Once activated, a virus will usually spread itself onto other systems – either across a network, via email, through the internet, or even via disks and CDs. A virus can delete or alter files and data, and may sometimes go to great lengths to remain undetected, and may often prove to be extremely difficult to remove. They often remain quite invisible to the unwary user, and may even disable anti-virus software to remain hidden and safe from detection and deletion. A trojan on the other hand is a standalone program. It does not add itself onto existing files, nor does it try to replicated and spread to other systems and networks. A trojan’s main purpose it to make it’s host system open to access, usually via the internet. A trojan may allow an unwanted person to see the files and data on the infected system. It may grant free access to the intruder, who may then be able to freely explore, view, modify and delete data from the hard drive. They may be able to intercept incoming and outgoing data, including emails, keystrokes, passwords, sensitive information and so on. For the Trojan to be effective, it needs to be run at every reboot of the infected system. Because of this it may add entries to the registry or even the startup folder. Removing the trojan tends to be quite simple. You simply delete the offending file, and remove all references to it. Detecting it, however, in the tens of thousands of files on most hard drives, is an altogether more difficult process.  |
|
|
| Total comments: 0 | |